March 21-25, 2022, students from the University of Advancing Technology (UAT) traveled to Ft. Lauderdale, Florida, to compete in the Maritime and Control Systems Cybersecurity Con, also known as Hack the Port 22. This hybrid cybersecurity event is hosted by MISI Academy (a STEM Mentoring Initiative) and DreamPort, and is inspired by U.S. Cyber Command.
According to Professor Aaron Jones, UAT’s Cyber Security Program Champion, attendees had an opportunity to attend lectures, speeches, and listen to panel discussions from government and industry leaders. Jeremy Bunce, UAT Cyber Program Support Specialist, led the team of cyber students to take on the challenge. The crew included Sam Roethemeyer, Christopher Barnes, Jerrod Touchton, Alexzander Rodriguez, and Emilio Cress. Here is Jeremy’s description of the experience:
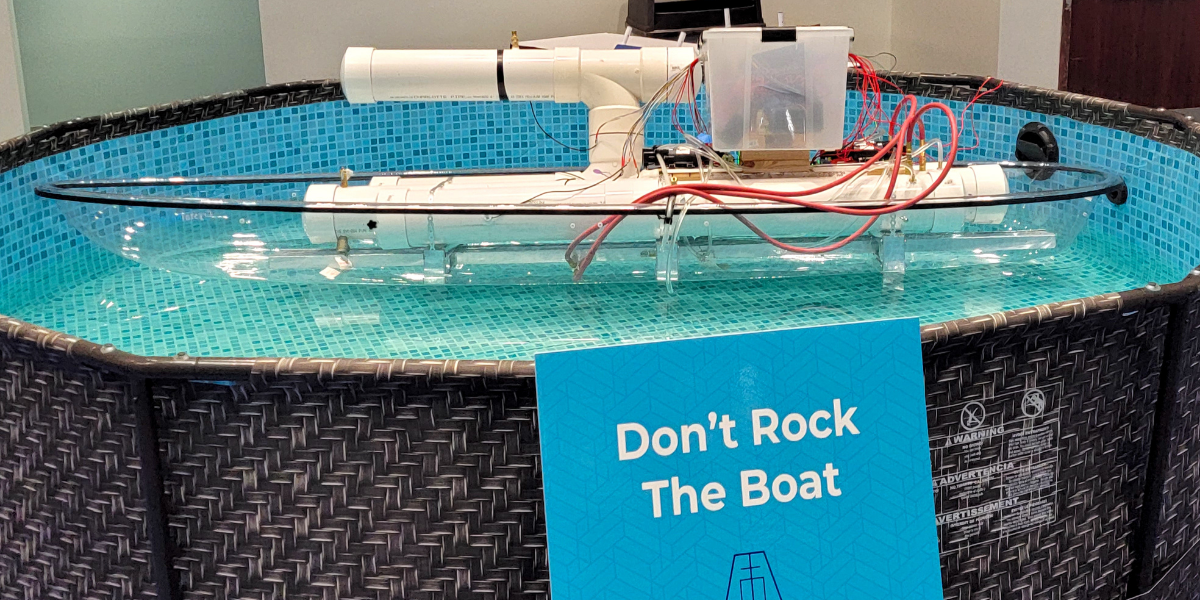
“The idea behind the hack the port competition was to simulate hacking into a port. They even had us go into Florida next to a real port to really sell the environment. The event also had physical devices to focus hacking into, such as a gas system, a boat, and even a crane.
On the first day, the students where tasked with starting in a foreign trade zone and getting into the network on the boat. This would be like the network version of getting past customs.
The UAT students tried two methods of attack: social engineering and making a back door. The social engineering method involved sending an email pretending to be students wanting a tour of their IT room to get the head of IT’s email. Once they got that, they sent an email pretending to be an employee needing their password because the internet was down. This was successful, and they got the head of IT’s username and password. The next step was to find what computer they could use that password for, but they were not successful in that.
For making a backdoor, the students were given a computer and had to put a virus on it to let them remotely access it. The first step was being able to log in. After many technical solutions, like getting into safe mode and recovery mode, the team accidentally discovered that the password they needed to enter was “password”. After a laugh, they moved on to getting an Administrator account that would let them write that virus. They were able to do this by being able to run a program called PowerShell and changing the password for the Administrator account, letting them log in. Then students tried to set up a program called RDP on that box to remotely access it. But unfortunately, they were not able to complete that by the end of the first day.
On the second day, the team was given access past the foreign trade zone and focused on how to hack the boat. One of the students was able to find a web page that showed the boat’s gas flow. Another was able to remotely control a computer on that boat but needed one more step to have full access. During this effort, a blue team was working on keeping them out, so they had to make sure to be stealthy to not be caught.
Here are some additional highlights:
- Jerrod got privilege escalation by seeing that you could run PowerShell as admin
- Team almost set up remote code exploit
- Chris worked on setting up a rubber ducky reverse shell in Python
- Sam found IP of box by filtering out syn packets only looking for the response
- Emilio Found the web server I/O by doing a rust scan and looking for a port that Emilio found though Wireshark
- Emilio found a website though Wireshark
- Jerrod research how to get into natural gas devices
- Jerrod got into a HLM website with the default password (monitoring the flow of gas)
Overall, the students learned a lot about how attackers get into the system, and all understand where to learn more since they were able to test their skills. And most importantly, they had a blast."
Well done to the students who attended and participated! It is important for cyber students to test their skills in games and competitions to prepare themselves for the challenges they will face after they complete their education.
“We are very proud of our students and firmly committed to developing the best security practitioners that we can,” said Professor Jones. “Our students are involved in missions that matter, and Hack the Port is another method by which we can provide hands on experience and instruction with the intent of preparing students for real life events and exercises.”

